Office documents, PDFs, CSVs, HTML, and more formats.
RAG as a Service
Any document, any format, and optimized output for the scenario, making RAG more than just Ready.

Automated optimal processing and knowledge graph construction in specific formats are all within reach.
It's not traditional ETL; only automated workflows can meet the demands of the AI era.
Cloud Identity Governance&Administration ——
Expand your digital platform into
Your identity center
All-in-one cloud security service, user directory, single sign-on, intelligent authorization...

Cloud Native
User and authentication connection services, SSO, authentication source integration, MFA all features ready to use, enabling you to quickly connect and embrace the SaaS ecosystem, accelerating enterprise digitalization
View MoreReal-time Synchronization
Support multiple IDP users and intelligent field matching, with incremental synchronization to multiple SaaS platforms
View MoreZero Development
Authentication source integration, application single sign-on, two-factor authentication, internal application access... No longer requires extensive development and customization, just configure in the console
View MoreAgent as a Service
Business applications, workstations, dashboards... wherever you need, we can help you integrate with intelligent agents, bringing intelligence seamlessly into your workflow.

We provide automated streams for real-time processing of enterprise application data and unstructured documents.
Supports various digital platforms and business systems like DingTalk, Feishu, WeCom, Slack, and more.
Use low-code methods to build and customize various tools for agents.
RAG as a Service
Any document, any format, and optimized output for the scenario, making RAG more than just Ready.

Office documents, PDFs, CSVs, HTML, and more formats.
Automated optimal processing and knowledge graph construction in specific formats are all within reach.
It's not traditional ETL; only automated workflows can meet the demands of the AI era.
Cloud Identity Governance&Administration ——
Expand your digital platform into
Your identity center
All-in-one cloud security service, user directory, single sign-on, intelligent authorization...

Cloud Native
User and authentication connection services, SSO, authentication source integration, MFA all features ready to use, enabling you to quickly connect and embrace the SaaS ecosystem, accelerating enterprise digitalization
View MoreReal-time Synchronization
Support multiple IDP users and intelligent field matching, with incremental synchronization to multiple SaaS platforms
View MoreZero Development
Authentication source integration, application single sign-on, two-factor authentication, internal application access... No longer requires extensive development and customization, just configure in the console
View MoreAgent as a Service
Business applications, workstations, dashboards... wherever you need, we can help you integrate with intelligent agents, bringing intelligence seamlessly into your workflow.

We provide automated streams for real-time processing of enterprise application data and unstructured documents.
Supports various digital platforms and business systems like DingTalk, Feishu, WeCom, Slack, and more.
Use low-code methods to build and customize various tools for agents.
RAG as a Service
Any document, any format, and optimized output for the scenario, making RAG more than just Ready.

Office documents, PDFs, CSVs, HTML, and more formats.
Automated optimal processing and knowledge graph construction in specific formats are all within reach.
It's not traditional ETL; only automated workflows can meet the demands of the AI era.
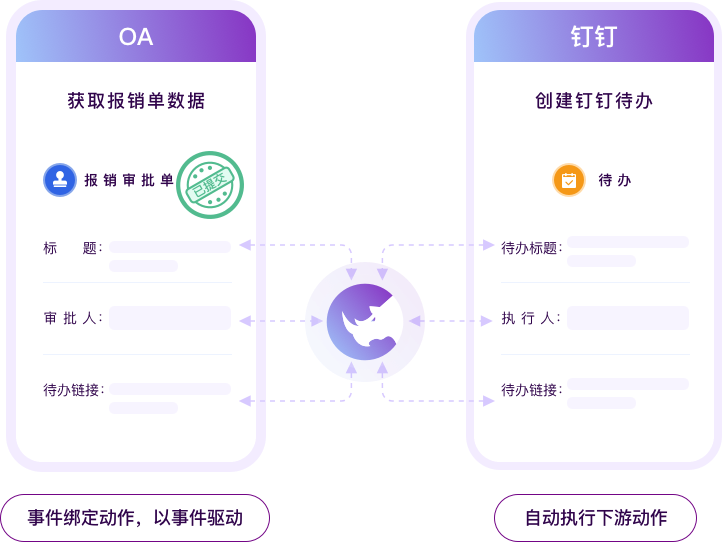
App Integration Platform - Empowering Business Digital Transformation
App integration platform, realizing data and process integration of multi-party applications, improving automation, intelligence and timeliness of fragmented businesses
Low-code data orchestration support, rich built-in applications, no development required, rapid implementation

Quickly solve business automation flow between applications
Triggers: Support system event triggers and scheduled tasks, meeting usage requirements for different scenarios;
Execute actions: Choose the desired action, such as sending a DingTalk to-do;
Data mapping: Achieve complex data associations between upstream and downstream different systems through low-code checkbox configuration.
Need to enhance security for digitalization?
Choose Digitalsee Zero Trust Components
From access control, detection to automated handling, One Stop zero trust security
Loading


